
Overview of Authentication Methods (Verification)
The physical verification process, as an authentication factor, is designed to verify the physical identity of a person. This verification becomes vital from a security perspective, since it validates the existence of the person.
There are basically three categories identified as authentication factors for physical verification.
Something that is,
- known by you; i.e. Password, Pin, Pattern, TOTP.
- possessed by you; i.e. Smartphone, Smartcard, USB token, or any other hardware key.
- physically unique to you; i.e. Face, Voice, Fingerprint.
Based on the above categories, there is a range of potential requirements that can be used to verify physical identity and authenticate access to websites, applications, networks, systems, and other types of secured services.
The list of authentication mechanisms used by cidaas to verify physical identity is shown below:
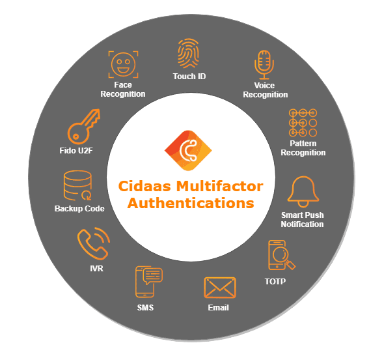
About MFA's
The following sections will take you through all the exclusive and secure physical verification methods offered by cidaas, with their details of configuration and usage. Here, we will also help you with the sign-up procedure and equip you with details on the mobile application's usage.
To start using the secure services of the cidaas authenticator, you will need to have a registered account with cidaas.
| cidaas Authentication mechanism | Description | Enrollment | Authentication |
|---|---|---|---|
| You enter the code sent to your registered email address. | How to configure Email | How to use Email | |
| Magic Link | The application sends a so-called Magic Link and keeps polling as long as the user successfully clicked on the link that was sent to the mail account. When this succeeds and the status switches to Verified, it can continue the authentication process | How to configure Magic Link | How to use Magic Link |
| Text message | Identification via a code that is sent to your phone via SMS. | How to configure Text message | How to use Text message |
| FIDO2/Passkeys/FIDO U2F | This standard uses a private and public key to validate your identity. | How to configure FIDO | How to use FIDO |
| TOTP Verification | Time-based One-time Password (TOTP) is a temporary passcode (six- or eight-digit) generated by an algorithm, used for authentication based on your time and device. | How to configure TOTP | How to use TOTP |
| Smart Push notification | Technique that uses the push notification feature of a mobile device and prompts you to choose the right code (as displayed on the web app) among a set of codes | How to configure push | How to use push |
| Touch ID Recognition | Biometric procedure to verify identity that is based on fingerprint | How to configure touch-id | How to use touch-id |
| Pattern Recognition | Identity verification that requires you to confirm a pattern, like those commonly used in mobile lock patterns. | How to configure pattern | How to use pattern |
| IVR Recognition | You enter the code that is prompted via a phone call as proof of your identity. | How to configure IVR | How to use IVR |
| Backup Code | An 8-digit backup code can be used to sign in to your account. | How to configure Backup-code | How to use Backup-code |
| Face Recognition | Identity verification using advanced biometric methods where the face is uniquely identified. | How to configure face-recognition | How to use face-recognition |
Need Support?
Please contact us directly on our support page.