cidaas as an Identity Provider
cidaas can act as an OpenID Connect (OIDC) Identity Provider (IdP) for external applications.
When integrated, cidaas provides single sign-on (SSO) and optional multi-factor authentication (MFA) to enhance application security.
Prerequisites
Before using cidaas as an OIDC Identity Provider, ensure:
- You have admin access to the cidaas Admin UI.
- An application (client) is created with the required redirect URLs.
- The client is configured with the
openidscope and any additional scopes needed. - Login providers or MFA settings are configured if required by your application.
How it Works
OIDC applications start an OAuth2 authorization flow and request authorization from the user.
During this flow, the client includes:
- the openid scope (required for OIDC), and
- any additional scopes needed to access user information.
Once the request is processed, the client receives:
- an access token, and
- an ID token issued by cidaas.
The ID token contains identity claims that enable the user’s SSO experience.
The client can also request additional information from the UserInfo endpoint.
OIDC further standardizes discovery, session management, and claim delivery beyond standard OAuth2.
cidaas as the IdP
When cidaas is configured as the identity provider:
- Users attempting to access a third-party application are redirected to cidaas for authentication.
- cidaas authenticates the user using credentials, or any of various passwordless verification methods (such as OTP, biometrics, etc.), along with configurable Multi-Factor Authentication (MFA), if enabled.
- After successful authentication, cidaas issues OIDC tokens. You can explore this flow firsthand and try out the authentication process via AuthKit.io.
- cidaas establishes an authenticated user session.
- The third-party application uses the ID token and access token to recognize the authenticated user. The access token can then be used for authorization when making API calls to the backend.
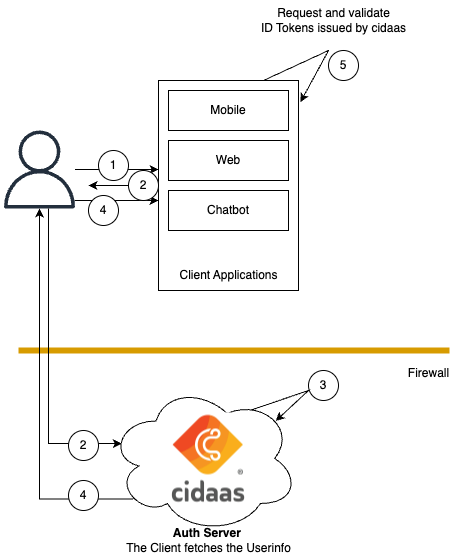
Authentication Flow Steps
- The user requests access to a client application.
- The application redirects the user to cidaas for authentication and requests the required tokens.
- cidaas authenticates the user using credentials, or any of the available passwordless verification methods (like OTP or biometrics), along with MFA if configured.
- Upon successful authentication, cidaas establishes an authenticated user session and issues an ID token and access token.
- The client application uses the ID token to recognize the authenticated user and can use the access token for making authorized API calls to the backend.
References
OpenID Connect is a well-documented specification. The following resources may support your setup:
Explore Related Topics
- OIDC Basics
- OAuth2 Flows
- App Management
- Client Secret Rotation
- Token Structure and ID Tokens
- Login Providers
- Session Management
Need help?
For assistance, visit our Support Portal.