User Field Settings
Configure what information users provide during registration and how it's stored.
Benefits
- Flexible User Identification: Email, mobile_number, and username can be used to identify users. Custom fields with
USERNAMEdata type can also be used as alternative login identifiers. - Customizable Field Structure: Configure field types, validation rules, and permissions to match your business requirements.
- Token Integration: Map fields to OAuth scopes to control which user data is included in tokens.
- Important Considerations:
- Field Key cannot be changed after creation - choose carefully
- Data Type can only be changed if the new type is compatible with the current one
Fields Explained
Fields define what information users provide during registration and how it's stored. The cidaas Admin Dashboard provides a visual interface for configuring field settings.
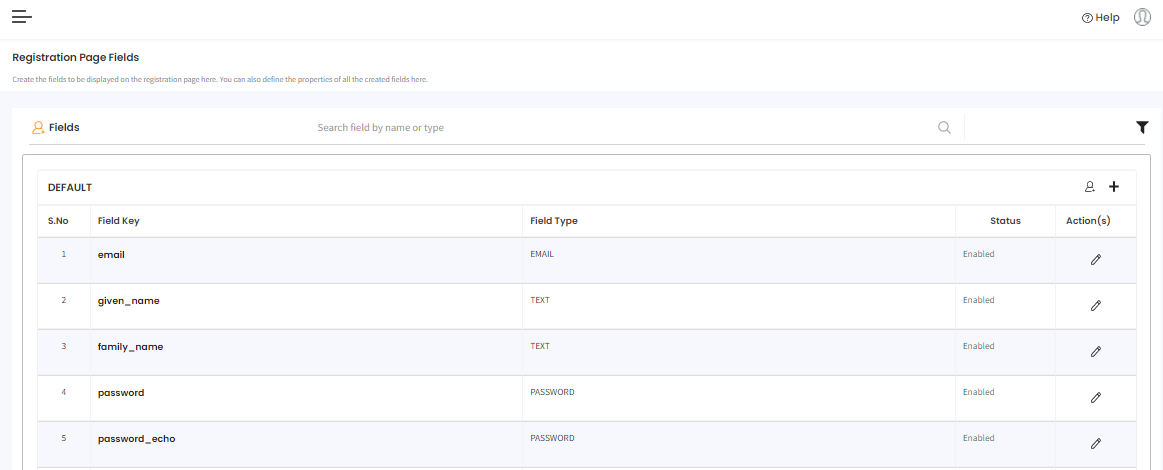
Registration Page Fields are the fields that appear on the registration form for end users. These fields can be configured based on your business requirements, including:
- Field Key: Unique identifier for the field (cannot be changed after creation)
- Field Type: Determines the input format and validation (see field types below)
- Status: Whether the field is enabled or disabled
- Permissions: Whether the field is required, read-only, internal, or unique
- Scopes: Which OAuth scopes the field belongs to (controls token inclusion)
Registration Page Fields can be accessed on the cidaas Admin dashboard under Settings > Registration field settings.
The following table view displays all configured fields:
Field Structure
A field setting consists of:
- a
dataTypeto be able to express semantics on a field and give hints for visual presentation - options to set editability and visibility of a field:
required,internal,readonly - options to use in resp. tokens using
scopes - grouping and ordering fields applying a virtual grouping by setting the
parent_group_idfor those fields you would like to add to theGROUPINGfield.orderingof fields to give fields an order in UI - setting field ranges with a
fieldDefinition - localize the
fieldKeyand editing hints in variouslocaleTexts
Field Setting can contain groups with the data type
GROUPINGwhich is used to group the Field Setting parameters that cannot be used directly for custom fields.
In addition to the default fields, cidaas lets you create and define custom registration page fields based on your business requirements.
To create or configure a custom field, navigate to Settings > Registration field settings in the cidaas Admin Dashboard and click Create Field.
Field Types
| Field Type | Description | Use Case |
|---|---|---|
| TEXT | Text input | Names, descriptions |
| Email address | User email (validated) | |
| MOBILE | Phone number | Mobile number (validated) |
| PASSWORD | Password field | User password (masked) |
| NUMBER | Numeric value | Age, quantity |
| DATE | Date and time | Birth date, event date |
| URL | Web link | Website, profile link |
| TEXTAREA | Multi-line text | Description, notes |
| SELECT | Dropdown selection | Single choice from options |
| MULTISELECT | Multiple selections | Multiple choices from options |
| RADIO | Radio buttons | Single choice (mutually exclusive) |
| CHECKBOX | Checkbox | Yes/No, true/false |
| CONSENT | Consent acceptance | GDPR consent tracking |
| USERNAME | Custom identifier | Alternative login identifier |
| ARRAY | Array of strings | List of values |
| JSON_STRING | JSON data | Structured data |
For SELECT, MULTISELECT, RADIO: Define the options (key-value pairs) users can choose from.
For DATE: Set date range (min/max dates).
For GROUPING: A special datatype used to create groupings of fields. Cannot store values, only used for UI organization to group related fields together. Can be used with Remote Fields to fetch data from external APIs.
Base Data Types
Since dataTypes reflect either a user interface type (like RADIO, TEXTAREA) and/or add semantics to the data (like PASSWORD, URL, EMAIL, CONSENT), the baseDataType is used to map the data to programming language data types and how data gets stored in databases (e.g., MongoDB, Elasticsearch).
| Data Type | Base Data Type | Description |
|---|---|---|
| TEXT | string | Text field with optional min/max length constraints |
| NUMBER | double/integer | Numeric field |
| RADIO | string | Predefined values, selected value saved as string |
| CHECKBOX | boolean | Binary value stored as boolean |
| PASSWORD | string | Text field with min/max length constraints |
| DATE | datetime | Date with optional min/max date constraints |
| URL | string | Text field that must match URL format |
| string | Text field that must match email format | |
| TEXTAREA | string | Multi-line text field |
| MOBILE | string | Text field that must match mobile number format |
| CONSENT | boolean | Binary value used to store consent |
| JSON_STRING | string | Text field for JSON data with optional min/max length |
| USERNAME | string | Text field for unique user identifiers |
| ARRAY | array[string] | Array of strings without predefined values |
| SELECT | string | Predefined values, selected value saved as string |
| MULTISELECT | array[string] | Predefined values, multiple selections saved as array of strings |
| DAYDATE | datetime | Date without time component (day/month/year only) |
| GROUPING | (none) | Note: GROUPING has no baseDataType. Special datatype for grouping fields. Cannot store values, only used for UI organization |
- Scopes: Select which OAuth scopes this field belongs to.
Scopes in Fieldsetup
What are Scopes?
Scopes control which fields are included in tokens. When an application requests specific scopes, only fields mapped to those scopes are returned.
How Scopes Work
- One field can be assigned to multiple scopes (e.g., Date of Birth in both "profile" and "personal" scopes)
- Multiple fields can share the same scope (e.g., First Name, Last Name, and email all in "profile" scope)
- When an application requests "profile" and "payment" scopes, only fields mapped to these scopes are included
- Fields without scopes are not included in tokens
Scope Model
The scope management system consists of three interconnected entities:
┌─────────────────────────────────────────────────────────────────┐
│ SCOPE MODEL │
├─────────────────────────────────────────────────────────────────┤
│ │
│ ┌──────────┐ assigned to ┌─────────────┐ │
│ │ Scope │◄──────────────────►│ Field │ │
│ └──────────┘ many-to-many └─────────────┘ │
│ │ │ │
│ │ requested by │ included in │
│ ▼ ▼ │
│ ┌──────────────┐ ┌─────────────┐ │
│ │ Application │───────────►│ Token │ │
│ │ │ requests │ (claims) │ │
│ └──────────────┘ └─────────────┘ │
│ │
└─────────────────────────────────────────────────────────────────┘
Key Relationships:
- Scope ↔ Field: Many-to-many relationship - one scope can include multiple fields, one field can belong to multiple scopes
- Application → Scope: Applications request specific scopes during authentication
- Scope → Token: Only fields mapped to requested scopes are included as claims in the token
Example:
- Field "email" mapped to scopes:
["email", "profile"] - Field "credit_card" mapped to scope:
["payment"] - Application requests scope:
"profile"→ Only "email" is returned (not "credit_card")
For more information, refer to Scope Management
- Permissions: Select one or more permissions:
| Permission | Description |
|---|---|
| Enable | Field is visible on the registration form |
| Required | Field is mandatory - user must provide input |
| Read Only | Field can be viewed but not changed by users |
| Internal | Field is hidden from users (admin only) |
| Unique | Field values must be unique across all users (e.g., employee ID) |
Permissions change depending on the field type selected.
-
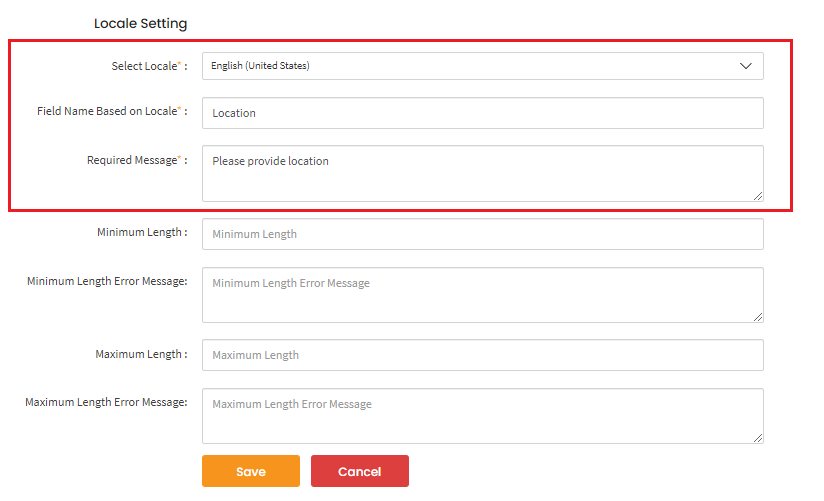
Localization (optional): Configure field labels and hints in different languages.
The
LocaleTextstructure provides localized labels and messages for a field. Each FieldSetup must have at least one LocaleText entry. Several LocaleText attributes are directly related to FieldDefinition attributes and provide localized messages for the corresponding validation constraints.Attribute Type Required Related FieldDefinition Description locale string Yes - Locale identifier (e.g., en,de,en-US,de-DE)name string Yes - Localized display name of the field minLength string No minLengthLocalized validation message when value is below minimum length maxLength string No maxLengthLocalized validation message when value exceeds maximum length required string No - Localized message shown when required field is empty matchWith string No matchWithLocalized error message when field values don't match the referenced field error string No regexLocalized error message displayed when regex validation fails attributes KeyValue[] Conditional attributesKeysLocalized display values for each key in attributesKeys. Required for SELECT, RADIO, MULTISELECTconsentLabel ConsentLabel No - Localized label and text for CONSENT type fields Note: For SELECT, RADIO, and MULTISELECT datatypes, the
attributesarray must contain a localized value for each key defined inFieldDefinition.attributesKeys. -
Validation Rules (optional):
The
Field Definitiondefines constraints and validation rules for a field. Different attributes apply depending on thedataType:Attribute Type Applicable DataTypes Description minDate datetime DATE, DAYDATE Minimum allowed date value maxDate datetime DATE, DAYDATE Maximum allowed date value initialDate datetime DATE, DAYDATE Default/initial date value initialDateView string DATE, DAYDATE Calendar view hint for UI: month,year, ormulti-yearminLength integer NUMBER, PASSWORD, URL, EMAIL, TEXTAREA, JSON_STRING, USERNAME Minimum length of field value (default: 0) maxLength integer NUMBER, PASSWORD, URL, EMAIL, TEXTAREA, JSON_STRING, USERNAME Maximum length of field value (default: 200) matchWith string TEXT, NUMBER, PASSWORD, URL, EMAIL, TEXTAREA, JSON_STRING, USERNAME fieldKeyof another field whose value this field must match (e.g., password confirmation)attributesKeys string[] SELECT (required), RADIO (required), MULTISELECT (required) Keys for predefined selection options regex string TEXT Regular expression pattern for field validation Validation Rules:
- Date constraints: If both
minDateandmaxDateare set,minDatemust be beforemaxDate. IfinitialDateis set, it must be betweenminDateandmaxDate. - Length constraints:
minLengthmust be less thanmaxLength. Both must be >= 0. Default values:minLength=0,maxLength=200. - Regex vs Length (TEXT datatype): For TEXT datatype,
minLength/maxLengthare deprecated. Useregexinstead. You can specify eitherregexorminLength/maxLength, but not both. - Selection types: For SELECT, RADIO, and MULTISELECT datatypes,
attributesKeysis required and must contain at least one key. Each key must have a corresponding localized value inLocaleText.attributes.
- Date constraints: If both
-
Click Save.
Important When you try to create a Field Setting that already exists, a notification window with the message "This Registration Field already exists" appears as shown below. The Field Key of a Field Setting must be unique.
System and Custom Fields
User fields are assigned to the user account:
- system fields "SYSTEM" - you can find in the identities of the user account
- custom fields "CUSTOM" - you can find in user accounts
customFieldssection
System fields are predefined fields that can be enabled or disabled in their field settings.
| fieldKey | dataType | enabled | scopes |
|---|---|---|---|
| yes | email, profile | ||
| given_name | TEXT | yes | profile |
| family_name | TEXT | yes | profile |
| password | PASSWORD | yes | |
| password_echo | PASSWORD | yes | |
| mobile_number | MOBILE | yes | phone |
| phone_number | MOBILE | no | phone |
| birthdate | DAYDATE | no | profile |
| middle_name | TEXT | no | profile |
| nickname | TEXT | no | profile |
| preferred_username | TEXT | no | profile |
| username | USERNAME | no | |
| profile | URL | no | profile |
| picture | URL | no | profile |
| website | URL | no | profile |
| gender | TEXT | no | profile |
| locale | TEXT | no | profile |
| address | GROUPING | no | profile |
| formatted | TEXT | no | profile |
| street_address | TEXT | no | profile |
| locality | TEXT | no | profile |
| region | TEXT | no | profile |
| postal_code | TEXT | no | profile |
| country | TEXT | no | profile |
How System Fields and Custom Fields Differ
The differences between the Custom and Default Field Settings are shown in the following table:
| Characteristic | System Field | Custom Field |
|---|---|---|
| Field Setting | YES ("fieldType" : "SYSTEM") | YES ("fieldType" : "CUSTOM") |
| Can be activated and deactivated? | YES | NO |
| Predefined Datatype | YES (modelled in SocialIdentity) | YES |
| Can be added? | NO | YES |
| Can be removed? | NO | YES |
| Can be individually grouped? | NO | YES |
Remote Fields
Remote Fields is a feature that allows field values to be fetched from an external API. This is configured on fields with dataType: GROUPING, where all child fields under the grouping are populated from the remote API response. The GROUPING itself does not hold values; child fields (field setups with parent_group_id set to this GROUPING's fieldKey) are what get filled from the API and appear in the token. The remote API response must be a JSON object whose keys match those child field keys.
Required: You need a GROUPING field with
remoteFieldSettings, at least one child field (withparent_group_idpointing to that GROUPING), and the grouping or its child fields added to the additional access token payload (see App Management). The payload configuration allows the system to fill child fields using the group's remote field settings. callOnce and apiClientSetup are required inremoteFieldSettings.
Remote Fields Configuration (GROUPING only)
Remote fields are configured using the remoteFieldSettings object, which is only applicable to fields with dataType: GROUPING:
| Attribute | Type | Required | Description |
|---|---|---|---|
| callOnce | boolean | Yes | When true, the API is called once per user (or when cache has expired); the result is stored in the user's customFields and reused for subsequent token requests until the system cache expires. When false, the remote API is called on every token request. |
| apiClientSetup | object | Yes | Configuration for the external API client including endpoint, protocol, and authentication |
System Defaults (not configurable):
- Cache time: Short-term cache duration for remote API responses (system managed)
- Timeout: Request timeout for remote API calls (system managed)
APIClientSetup and APIAccessSetup Structure
The apiClientSetup object defines how to communicate with the external API, including endpoint configuration and authentication.
Important: The communicationEP is recommended to be a GET API endpoint that includes an identifier parameter placeholder. Use the same placeholder syntax as in the table above:
- User identifier:
identifier={{userId}}— replaced with a cidaas user identifier (sub,email,mobile,username, or custom field with dataTypeUSERNAME) - Custom field:
identifier={{customFields.fieldKey}}— replaced with the value from the user's custom field (e.g.{{customFields.insuranceNumber}})
The placeholder is replaced at runtime with the actual value before making the API call.
Note: Remote Fields use the same authentication structure as webhooks. Authentication is configured inside apiAccess (nested under apiClientSetup):
apiAccesscontains:apiAccessType:APIKEY|TOTP|BASIC_AUTH|GEN_OAUTH2|CIDAAS_OAUTH2- One detail object based on
apiAccessType:apikeyDetails- forAPIKEYauthenticationtotpDetails- forTOTPauthenticationbasicAuthDetails- forBASIC_AUTHauthenticationoAuthDetails- forCIDAAS_OAUTH2andGEN_OAUTH2authentication
| Auth Type | Security Level | Description |
|---|---|---|
APIKEY | low | The pre-shared API key which has to be verified by the remote API |
TOTP | medium | The time-based one-time-password (TOTP) generated with the TOTP key that is provided |
BASIC_AUTH | medium | Basic authentication using username and password credentials for the remote API |
CIDAAS_OAUTH2 | high | Security with client credentials grant flow where pre-defined scopes should be set in the remote API service. Since the clientId is not shared with anyone and scopes can be applied, it could be considered the most secure |
GEN_OAUTH2 | high | Security with client credentials grant flow that requires a well-known client secret and scopes that should be requested from the remote API service |
For detailed specification of APIClientSetup and authentication detail structures, see the API Access Specification.
Remote API Requirements
The remote API must fulfill the following requirements:
| Requirement | Description | Example |
|---|---|---|
| HTTP Method | Recommended to be a GET endpoint | GET https://api.example.com/data |
| Identifier Parameter | The URL must contain an identifier parameter with a placeholder that will be replaced at runtime | https://myexternal-service.de?identifier={{customFields.insuranceNumber}} |
| Placeholder Formats | User identifier: identifier={{userId}} — replaced with sub, email, mobile, username, or custom field with dataType USERNAMECustom field: identifier={{customFields.fieldKey}} — replaced with actual value from user's custom field | identifier={{sub}}identifier={{customFields.insuranceNumber}} |
| Response Format | Must return a JSON object with field keys matching the child fields of the grouping | { "fieldKey1": "value1", "fieldKey2": "value2"} |
| Authentication | Must accept one of the supported apiAccessType values defined in apiClientSetup | APIKEY, TOTP, or CIDAAS_OAUTH2 |
Note: At runtime, placeholders like {{customFields.insuranceNumber}} will be replaced with the actual value from the user's customFields.insuranceNumber field.
Access Token Payload Configuration
The additional access token payload accepts either the GROUPING field or its child fields (or both). When you add the grouping or any of its child fields to the additional access token payload, the system uses the group's remote field settings (remoteFieldSettings) to call the remote API and fill those child fields for the token. Configure the additional access token payload in App Management (application token settings).
Data Flow Overview
┌─────────────────┐ ┌─────────────────┐ ┌──────────────────┐
│ User Login │────▶│ token-srv │────▶│ Check Grouping │
└─────────────────┘ │ (token request) │ │ remoteFieldSettings? │
└─────────────────┘ └────────┬─────────┘
│
┌────────────────────────┴─────────────────────────────┐
│ │
▼ YES ▼ NO
┌───────────────────┐ ┌───────────────┐
│ Check callOnce? │ │ No fields │
└─────────┬─────────┘ │ returned │
│ └───────────────┘
┌─────────────────┴─────────────────┐
│ │
▼ callOnce: true ▼ callOnce: false
┌───────────────────────┐ ┌───────────────────────┐
│ Check user customFields│ │ Authenticate │
│ for persisted data │ │ (apiAccessType) │
└───────────┬───────────┘ └───────────┬───────────┘
│ │
┌───────────┴───────────┐ │
│ │ │
▼ Data exists ▼ No data │
┌───────────────────┐ ┌───────────────┐ │
│ Use persisted │ │ Authenticate │ │
│ customFields for │ │ (apiAccessType) │ │
│ token payload │ └───────┬───────┘ │
└──────�─────────────┘ │ │
│ │
▼ ▼
┌───────────────────┐ ┌───────────────────┐
│ Call Remote API │ │ Call Remote API │
└───────────┬───────┘ └───────────┬───────┘
│ │
▼ ▼
┌───────────────────────┐ ┌───────────────────────┐
│ Persist data in user │ │ Use data for │
│ customFields │ │ token payload │
└───────────┬───────────┘ └───────────────────────┘
│
▼
┌───────────────────────┐
│ Use data for │
│ token payload │
└───────────────────────┘
Error Handling and Logging
Important: If a remote field is not returned in the API response payload, the field will not be added to the token. This is silent behavior - the token will simply not contain that field.
Proper logging must be implemented for:
- Failed requests: Log when the external API returns an error response (4xx, 5xx status codes)
- Timed out requests: Log when the external API does not respond within the configured timeout
- Missing fields: Log when expected fields are not present in the API response
- Authentication failures: Log when the API authentication fails (OAuth2 token generation, invalid API key, etc.)
Example: Remote Field Setup for GROUPING
Example with CIDAAS OAuth2 Authentication (3.102.4 structure):
{
"fieldKey": "external_customer_data",
"dataType": "GROUPING",
"fieldType": "CUSTOM",
"enabled": true,
"remoteFieldSettings": {
"callOnce": true,
"apiClientSetup": {
"communicationEP": "https://myexternal-service.de?identifier={{customFields.insuranceNumber}}",
"httpMethod": "GET",
"apiAccess": {
"apiAccessType": "GEN_OAUTH2",
"oAuthDetails": {
"client_id": "my-client-id",
"client_secret": "my-client-secret",
"req_scopes": "ext:customservice_read",
"wellknownUrl": "https://auth.extidp.com/.well-known"
}
}
}
}
}
Note: At runtime, {{customFields.insuranceNumber}} will be replaced with the actual value from the user's customFields.insuranceNumber field. Alternatively, you can use identifier={{sub}} to use a user identifier (sub, email, mobile, username).
Example with API Key Authentication (3.102.4 structure):
{
"fieldKey": "external_data",
"dataType": "GROUPING",
"fieldType": "CUSTOM",
"enabled": true,
"remoteFieldSettings": {
"callOnce": false,
"apiClientSetup": {
"communicationEP": "https://api.example.com/data?identifier={{sub}}",
"httpMethod": "GET",
"apiAccess": {
"apiAccessType": "APIKEY",
"apikeyDetails": {
"apikey": "your-api-key-value",
"apikey_placeholder": "X-API-Key",
"apikey_placement": "header"
}
}
}
}
}
Child fields under this grouping (with parent_group_id: "external_customer_data") will be populated from the remote API response.
Example cURL requests (remote fields, 3.102.4)
The following examples create GROUPING fields with remoteFieldSettings using the apiAccess structure. Set BASE_URL to your cidaas host (e.g. https://your-tenant.cidaas.eu) and AUTH_HEADER to a valid Bearer token (e.g. Authorization: Bearer <access_token>).
1. APIKEY
curl --location "${BASE_URL}/fieldsetup-srv/fields" \
--header "$AUTH_HEADER" \
--header 'Content-Type: application/json' \
--data '{
"parent_group_id": "DEFAULT",
"dataType": "GROUPING",
"fieldKey": "remote_apikey_field",
"fieldType": "CUSTOM",
"scopes": ["profile"],
"localeTexts": [{ "locale": "en-US", "name": "Remote API Key field" }],
"remoteFieldSettings": {
"apiClientSetup": {
"communicationEP": "https://api.example.com/users?identifier={{sub}}",
"httpMethod": "GET",
"apiAccess": {
"apiAccessType": "APIKEY",
"apikeyDetails": {
"apikey": "your-api-key",
"apikey_placeholder": "X-Api-Key",
"apikey_placement": "header"
}
}
},
"callOnce": false
}
}'
2. TOTP
curl --location "${BASE_URL}/fieldsetup-srv/fields" \
--header "$AUTH_HEADER" \
--header 'Content-Type: application/json' \
--data '{
"parent_group_id": "DEFAULT",
"dataType": "GROUPING",
"fieldKey": "remote_totp_field",
"fieldType": "CUSTOM",
"scopes": ["profile"],
"localeTexts": [{ "locale": "en-US", "name": "Remote TOTP field" }],
"remoteFieldSettings": {
"apiClientSetup": {
"communicationEP": "https://api.example.com/users?identifier={{sub}}",
"httpMethod": "GET",
"apiAccess": {
"apiAccessType": "TOTP",
"totpDetails": {
"totpkey": "base32-secret",
"totp_placeholder": "X-Totp-Key",
"totp_placement": "header"
}
}
},
"callOnce": true
}
}'
3. BASIC_AUTH
curl --location "${BASE_URL}/fieldsetup-srv/fields" \
--header "$AUTH_HEADER" \
--header 'Content-Type: application/json' \
--data '{
"parent_group_id": "DEFAULT",
"dataType": "GROUPING",
"fieldKey": "remote_basicauth_field",
"fieldType": "CUSTOM",
"scopes": ["profile"],
"localeTexts": [{ "locale": "en-US", "name": "Remote Basic Auth field" }],
"remoteFieldSettings": {
"apiClientSetup": {
"communicationEP": "https://api.example.com/users?identifier={{sub}}",
"httpMethod": "GET",
"apiAccess": {
"apiAccessType": "BASIC_AUTH",
"basicAuthDetails": {
"user": "api-user",
"password": "api-password"
}
}
},
"callOnce": false
}
}'
4. CIDAAS_OAUTH2
curl --location "${BASE_URL}/fieldsetup-srv/fields" \
--header "$AUTH_HEADER" \
--header 'Content-Type: application/json' \
--data '{
"parent_group_id": "DEFAULT",
"dataType": "GROUPING",
"fieldKey": "remote_cidaas_oauth2_field",
"fieldType": "CUSTOM",
"scopes": ["profile"],
"localeTexts": [{ "locale": "en-US", "name": "Remote Cidaas OAuth2 field" }],
"remoteFieldSettings": {
"apiClientSetup": {
"communicationEP": "https://qc-wimcon1-test-01-v3-prod.cidaas.eu/user-srv/users?identifier={{sub}}",
"httpMethod": "GET",
"apiAccess": {
"apiAccessType": "CIDAAS_OAUTH2",
"oAuthDetails": {
"client_id": "YOUR_CLIENT_ID",
"req_scopes": "cidaas:users_read"
}
}
},
"callOnce": true
}
}'
5. GEN_OAUTH2
curl --location "${BASE_URL}/fieldsetup-srv/fields" \
--header "$AUTH_HEADER" \
--header 'Content-Type: application/json' \
--data '{
"parent_group_id": "DEFAULT",
"dataType": "GROUPING",
"fieldKey": "remote_gen_oauth2_field",
"fieldType": "CUSTOM",
"scopes": ["profile"],
"localeTexts": [{ "locale": "en-US", "name": "Remote Gen OAuth2 field" }],
"remoteFieldSettings": {
"apiClientSetup": {
"communicationEP": "https://api.example.com/users?identifier={{sub}}",
"httpMethod": "GET",
"apiAccess": {
"apiAccessType": "GEN_OAUTH2",
"oAuthDetails": {
"client_id": "external-client-id",
"client_secret": "external-client-secret",
"wellknownUrl": "https://auth.example.com/.well-known/openid-configuration",
"req_scopes": "openid profile"
}
}
},
"callOnce": true
}
}'
Technical Integration
The field setup can also be managed using the field setup API.
| API | Description | Link |
|---|---|---|
| Store a field setup | Create or update a field setup | API Reference |
| Find field setups | Search fields using graph filters | API Reference |
| Get field setup | Get field setup by fieldKey | API Reference |
| Delete field setup | Delete field setup by fieldKey | API Reference |
| Update field order | Update registration field order | API Reference |
Capturing User Consents during Registration
Consents provide a legal basis to collect and use personal data from users. One place where companies may choose to collect consent according to the GDPR is on the registration page of an application.
In the registration flow, a business is not only collecting attributes like name and email, but also meets business requirements. Assuming that a company is using consent as a basis to collect personal data and use it for security & analytics, when an individual opts in, the form collects the given consent as an attribute from the individual to track who has consented.
It's important to note how consent flows can be designed. You can add/edit consents during registration and login. Learn more about Consent Management.