Cspace certificates
This article will help you add a custom domain or certificate via Cspace.
We will demonstrate to you:
- How to add a custom domain or certificate.
- How to update a custom domain or certificate.
How to add custom domain or certificate
-
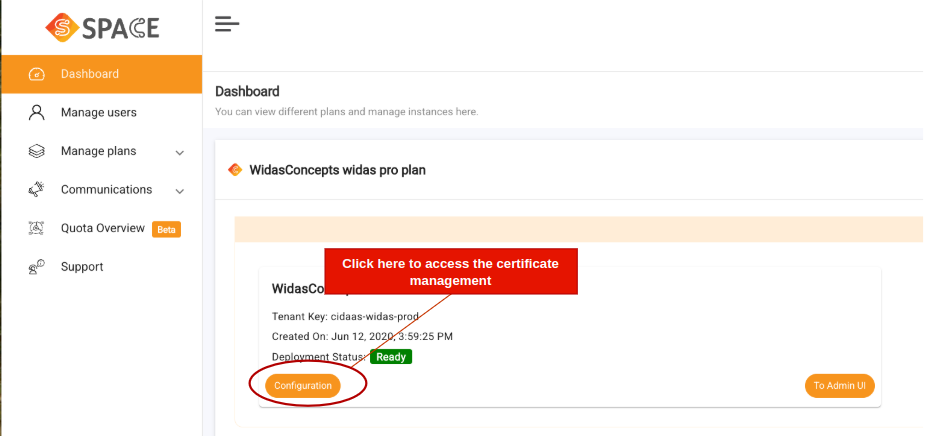
Login to your Cspace.
-
On the Dashboard, Select your instance plan.
-
Click on configuration and click + icon under Certificate Management tab.
Before proceeding further, make sure that you have added a CNAME entry in your DNS pointing to the custom domain you want to add to the cidaas domain displayed. Example: widas-test.cidaas.eu
-
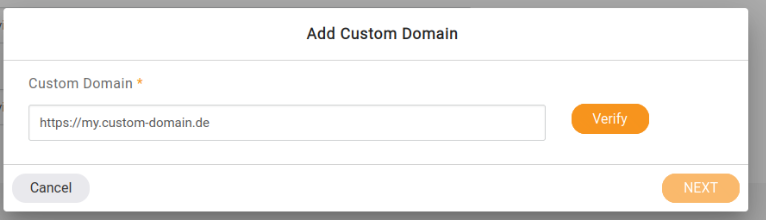
Click on next and enter your custom domain, and click on verify.
- We verify the domain is pointing to our cname; if it is not, you will be notified; otherwise, If it is pointing to our cname, it will let you continue with the setup.
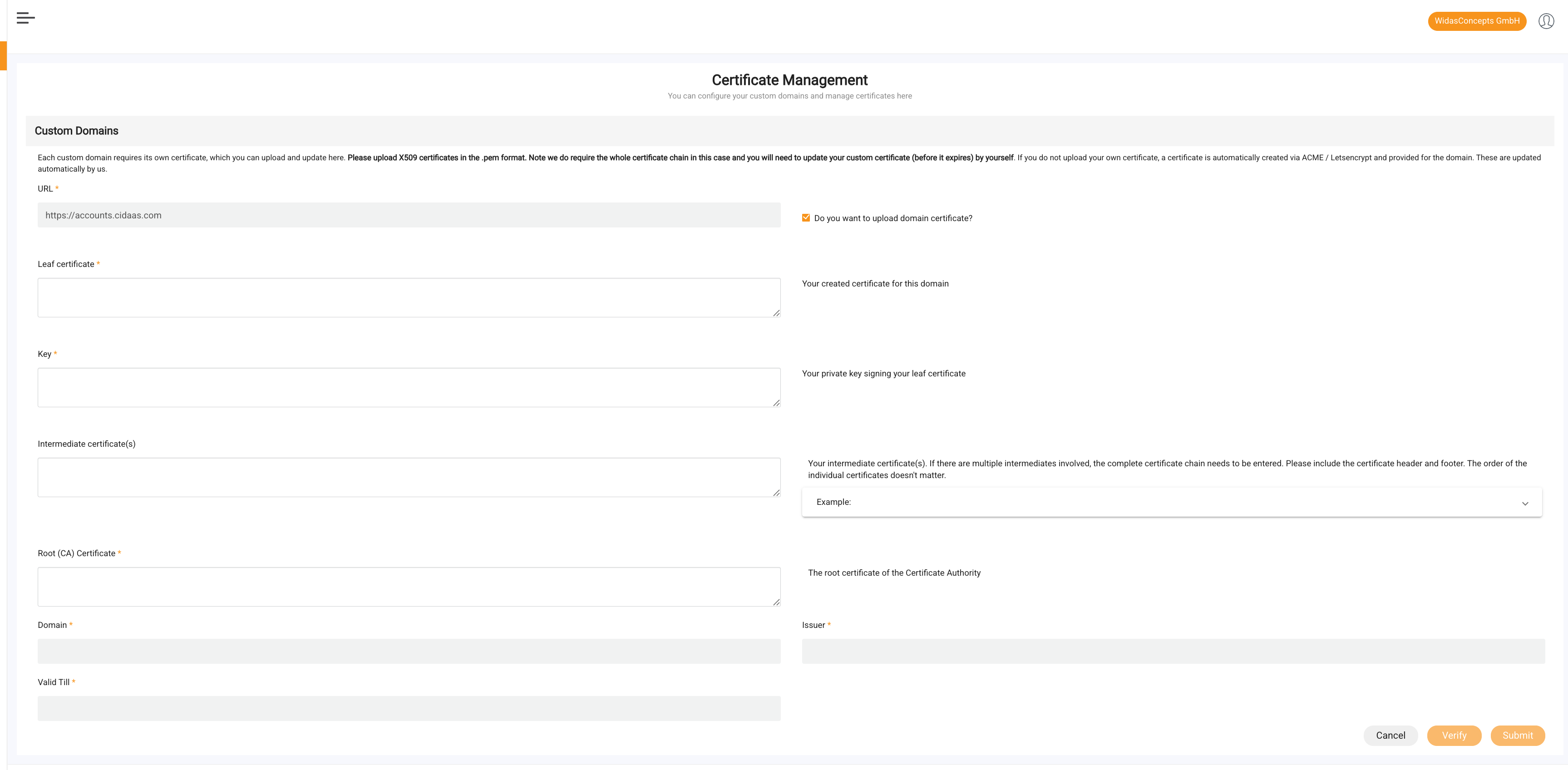
Next, it will ask you if you want to upload a custom certificate for this domain. If you want to entrust us with the certificate management, you have to do nothing else and just save the domain without uploading a custom certificate. Then we will create a certificate for you via Letsencrypt and manage the certificate lifecycle on our own.
- We verify the domain is pointing to our cname; if it is not, you will be notified; otherwise, If it is pointing to our cname, it will let you continue with the setup.
If you want to use a custom certificate, you will have to update it yourself. We have demonstrated it for you in the next section.
How to update your custom certificate
-
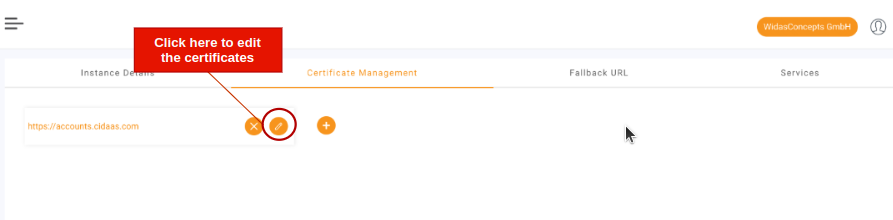
Login to your Cspace.
-
On the Dashboard, Select your instance plan.

-
Click on configuration and click on edit icon under Certificate Management tab.
-
Update all the required certificates.
| Component | Description | Purpose / Role | Issued By | Stored Where |
|---|---|---|---|---|
| Root Certificate | The top-most certificate in a certificate chain. It is self-signed and trusted by systems implicitly or via manual installation. | Serves as the trust anchor for all other certificates in the chain. Verifies intermediate and leaf certificates. | Self-signed (Root CA) | OS/browser trust store |
| Intermediate Certificate | A certificate issued by the Root CA (or another intermediate CA) to create a chain of trust. | Acts as a bridge between the root certificate and the leaf certificate. Adds a layer of security by isolating root CA from end-user operations. | Root CA or another Intermediate CA | Installed on servers or client systems |
| Leaf Certificate | The end-entity certificate used by websites or services. Also known as the server certificate or end-entity certificate. | Authenticates a specific domain or user. Used in HTTPS (SSL/TLS) to secure connections. | Intermediate CA | On the web server or client device |
| Key (Private/Public) | Cryptographic keys used to encrypt/decrypt data. Comes in pairs: private (kept secret) and public (shared). | Private Key signs data; Public Key verifies signature. The private key is bound to the leaf certificate. | Generated during CSR process | Private key: secure server location Public key: in certificate |
PEM Certificate & Key Format Markers
| Type | Start Marker | End Marker | Description |
|---|---|---|---|
| Root / Intermediate / Leaf Certificate | -----BEGIN CERTIFICATE----- | -----END CERTIFICATE----- | Base64-encoded X.509 certificate (used for SSL/TLS). Can be root, intermediate, or leaf cert. |
| Private Key (unencrypted) | -----BEGIN PRIVATE KEY----- | -----END PRIVATE KEY----- | PKCS#8 format private key (can be RSA, EC, etc.) |
Example: Leaf Certificate
-----BEGIN CERTIFICATE-----
MIIDXTCCAkWgAwIBAgIJAK5tXYv1eqksMA0GCSqGSIb3DQEBCwUAMEUxCzAJBgNV
...
-----END CERTIFICATE-----
Notes
- These are always Base64-encoded DER representations of the certificate or key.
- They’re used in many systems like Apache, Nginx, Kubernetes, OpenSSL, etc.
- Tools like
opensslcan convert between PEM and DER (binary) formats if needed.
How to verify the successful update
Each certificate is digitally signed by its issuer. For example: It verifies that the intermediate certificate’s signature matches the root CA’s public key, and so on.
- The root certificate is checked against the client’s trusted CA list.
- If the root is trusted → the chain is valid. Domain match: The domain the client connected to must match the Common Name or SAN in the leaf certificate.
Time validity: Current date must be within the Not Before and Not After range.
How you can check
- Open the Website (your domain)
- Click the Padlock Icon
- View Certificate Details
Help and support
Please contact us directly on our support page.