
Auth Manager
Auth Manager is cidaas's enterprise authorization platform that bundles multiple groups and roles into reusable templates representing job functions or positions. Instead of manually assigning individual permissions, templates define complete access profiles that grant users all necessary groups and roles across multiple applications, systems, and locations in a single request.
Core Concept: Function-Based Access
Auth Manager templates represent enterprise functions (e.g., "Presales Person", "Project Manager", "Regional Sales Lead"). Each template bundles:
- Multiple groups across different applications
- Multiple roles within those groups
- Cross-system access (CRM, ERP, collaboration tools, etc.)
- Location-based permissions (office access, regional systems, etc.)
Example: A "Presales Person" template might grant:
- Group:
sales-teamwith rolepresalesin CRM application - Group:
product-accesswith roleviewerin product catalog - Group:
regional-westwith rolememberfor location-based access - Group:
demo-environmentwith roletesterfor demo systems
All assigned with one template and one approval.
Benefits
Efficiency Gains
- Self-Service: Users request complete access profiles without IT tickets
- Automated Workflows: All permissions assigned automatically upon approval
- Time Savings: Reduce manual permission management by 80%+
- Faster Onboarding: New employees get complete access in hours, not days
Security & Compliance
- Time-Bound Access: Permissions automatically expire when no longer needed
- Approval Workflows: Multi-level approvals for sensitive access profiles
- Audit Trail: Complete history of who requested, approved, and received access
- Least Privilege: Grant access only for required duration
Better Governance
- Centralized Management: All permissions managed through function templates
- Consistent Policies: Standardized approval processes across organization
- Visibility: Track all authorization requests and their status
- Compliance Ready: Automated access reviews for regulatory requirements
Terminology
Key Terms
| Term | Definition |
|---|---|
| UAT | User Authorization Template - A reusable blueprint bundling multiple groups/roles into an enterprise function |
| UAR | User Authorization Request - A specific request for access using a UAT |
| Requestor | User who creates an authorization request (can be for themselves or others) |
| Approver | User who can approve or reject authorization requests |
| Designated User | Target user who will receive the permissions if request is approved |
| Template Status | Current state: inProgress, active, inActive, archived |
| Request Status | Current state: pending, granted, assigned, rejected, completed |
| Approval Sequence | Order: SEQUENTIAL_ALL, PARALLEL_ALL, and PARALLEL_ONE |
| Valid From | Start date/time when permissions become active |
| Valid Until | End date/time when permissions expire (empty = permanent) |
Request Status Flow
| Status | Description | What Happens Next |
|---|---|---|
pending | Request submitted, awaiting approval | Approvers can review and approve/reject |
granted | Request approved, permissions not yet assigned | System automatically assigns when validFrom date arrives |
assigned | Permissions are active | User has access; expires when validUntil date arrives |
rejected | Request denied | No permissions granted |
completed | Access period expired | Permissions automatically revoked |
Approval Sequences
| Sequence Type | Description | Use Case |
|---|---|---|
| SEQUENTIAL_ALL | All approvers must approve in order | High-security scenarios requiring multiple approvals |
| PARALLEL_ALL | All approvers must approve (any order) | Multiple stakeholders need to agree |
| PARALLEL_ONE | Any single approver can approve | Fast approval for low-risk permissions |
Good To Know
Template Visibility
- Active templates only: Non-admin users can only see and use
activetemplates - Admin access: Users with
AUTHTEMPLATE_ADMIN_GROUPMAProle can see all template statuses - Template filtering: Users only see templates they're allowed to use (based on requestor rules)
Permission Assignment
- Automatic assignment: Permissions assigned when request is
grantedandvalidFromdate has arrived - Automatic revocation: Permissions removed when
validUntildate arrives or request isrejected/completed - Future-dated: Set
validFromin the future to schedule access activation
Best Practices
- Clear naming: Use descriptive template names (e.g., "Presales Person - West Region")
- Bundle related access: Group all permissions needed for a function together
- Time limits: Set
validUntilfor temporary access - Test first: Create template in
inProgressstatus, test, then activate
Technical APIs
API Overview
Base URL: {{your-domain}}/userauthmanager
Authentication
- User Token:
cidaas:userauth_mgmt+ group roleAUTHTEMPLATE_ADMIN_GROUPMAP - Client Credentials:
cidaas:userauth_template_write
Request Example
How to create user authorization template?
The User authorization template comprises groups, roles, approvers, requesters, and the types of approvals. You can use this template multiple times to request access for others or yourself.
Step 1: Access Template Creation
- Log in to the Auth Manager Dashboard
- Navigate to the Approve authorization requests tab
- Click on the Create authorization template icon
Step 2: Configure Basic Information
-
Template Name: Enter a descriptive name for your template (e.g., "Admin Access Request")
-
Description: Provide a clear description of what this template is for
-
Template Type: Select the appropriate type (typically "usergroupmap" for group/role assignments)
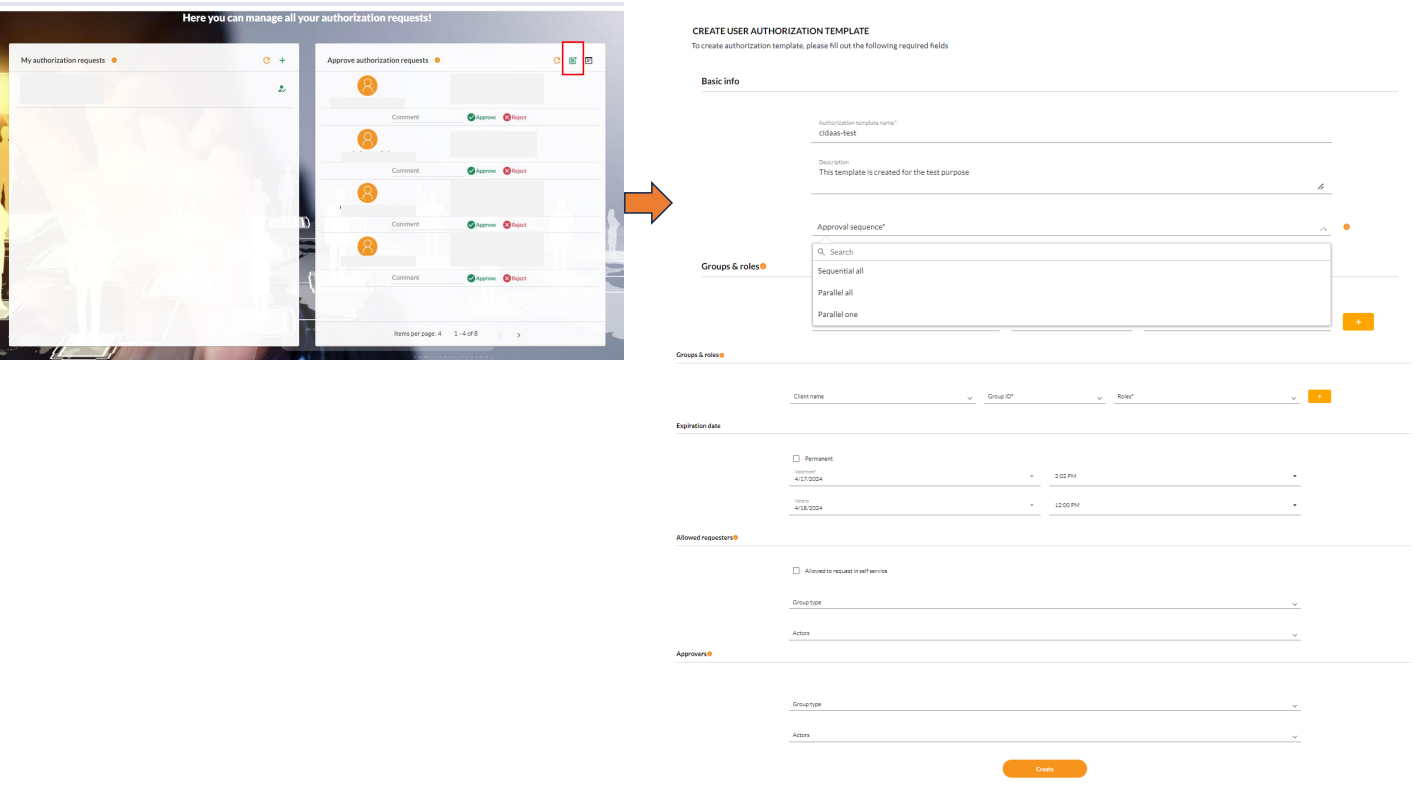
Step 3: Set Approval Sequence
Choose how approvals should be processed:
- Sequential: Approvals must be granted in the exact order specified in the approvers list. Each approver must approve before the next one can act.
- Parallel All: All approvers must approve, but they can do so in any order. Access is granted only when everyone has approved.
- Parallel One: Any single approver can approve the request. Access is granted as soon as one approver approves.
Step 4: Define Groups and Roles
- Click Add Group/Role to specify what permissions this template grants
- For each entry, specify:
- Client Name: The application or system this applies to
- Group ID: The specific group to assign users to
- Roles: The roles to assign within that group
- You can add multiple group/role combinations for complex permission sets
Step 5: Set Validity Period
- Valid From: Set the start date when this template becomes active
- Valid To: Set the end date when this template expires
- Leave empty for permanent templates
- Set specific dates for time-limited access
Step 6: Configure Allowed Requesters
Define who can use this template to request access:
- Self Requests: Enable if users can request access for themselves
- Specific Users: Add individual user IDs who can make requests
- Group Filters: Specify groups whose members can make requests
- Set group type (e.g., "MANAGER_GROUP")
- Define role filters within those groups
- Choose match condition (AND/OR)
Step 7: Define Approvers
Specify who can approve requests made with this template:
- Actor Subs: Add specific user IDs who can approve
- Group Filters: Define groups whose members can approve
- Set group type (e.g., "ADMIN_GROUP")
- Define role filters (e.g., "GROUP_ADMIN")
- Choose match condition (AND/OR)
Step 8: Configure Designated Users (Optional)
If applicable, specify which users this template can be applied to:
- Group Filters: Define target groups for the template
- Role Filters: Specify roles within those groups
- Match Conditions: Set how multiple criteria should be evaluated
Step 9: Create and Test the Template
- Review all configuration settings
- Click Create to save the template
- Test the template by making a sample request
- Verify that the approval workflow functions as expected
Step 10: Manage Existing Templates
- Click on the View user authorization template (UAT) icon in the Approve authorization requests tab
- View, edit, or delete existing templates as needed
- Monitor template usage and effectiveness
API Reference
For developers integrating with the Auth Manager Dashboard, see the User Authorization Management API for complete API documentation and endpoints.
How to request new authorization?
Step 1: Access Authorization Request
- Log in to the Auth Manager Dashboard
- Navigate to the My authorization requests tab
- Click on the New authorization request icon
Step 2: Select Authorization Template
- From the dropdown list, select the appropriate authorization template
- Review the template details to understand what permissions you're requesting
- Ensure you have the right to use this template (check allowed requesters)
Step 3: Specify Request Details
- Request Type: Choose whether you're requesting for:
- Yourself: Request access for your own account
- Others: Request access for another user or multiple users
- Target User(s): If requesting for others, specify:
- User email addresses
- User IDs
- Or select from a user list (if available)
- Reason: Provide a clear business justification for the access request
- Explain why this access is needed
- Include any relevant context or urgency
Step 4: Set Access Duration
- Access Duration: Specify how long the requested access should last:
- Permanent: Access remains until manually revoked
- Time-limited: Set specific start and end dates
- Duration-based: Set access for a specific number of days/weeks/months
- Start Date: When should the access begin (if applicable)
- End Date: When should the access expire (if time-limited)
Step 5: Review and Submit
- Review all request details for accuracy
- Verify that the template, users, and duration are correct
- Check that your reason is clear and justified
- Click Send to submit the authorization request
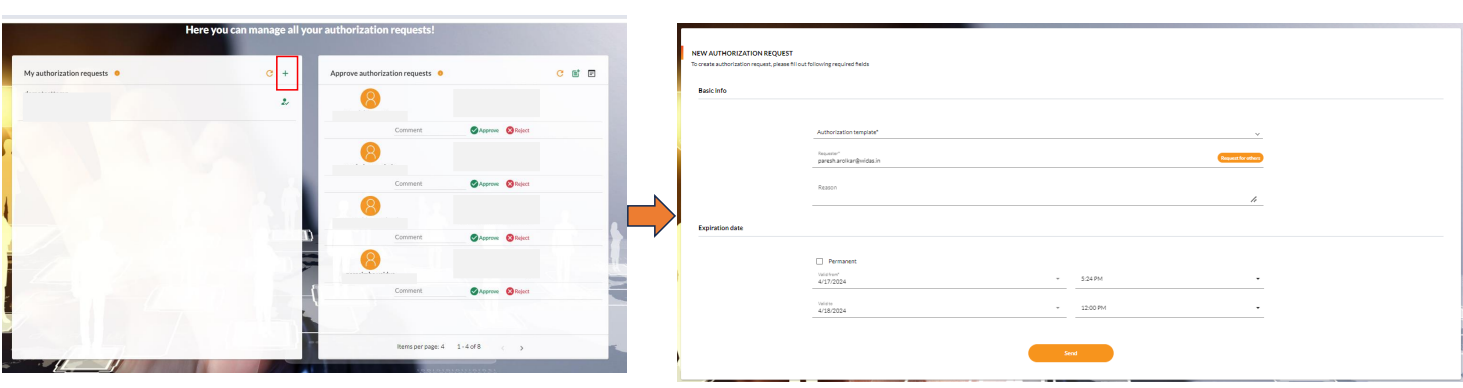
Step 6: Monitor Request Status
- After submission, you'll receive a confirmation
- Monitor the request status in the My authorization requests tab
- Check for notifications about approval progress
- Respond to any questions from approvers if needed
Status in Auth manager
Approved ✅ : This status states that the request is approved, but the groups and roles are yet to be assigned.
Assigned 🙋♂️✅:This status states that the request is approved and groups and roles are assigned.
Rejected ❌ : This status states that the request is rejected.
Scale your Auth Manager for different layouts
The URL pattern follows a consistent structure to ensure easy navigation and maintenance.
URL Pattern:
Key Endpoints
| API | Description | Link |
|---|---|---|
| Create User Authorization Template | Creates a new User Authorization Template (UAT) for managing user group assignments and authorization workflows. | View API |
| Get User Authorization Template by ID | Retrieves a specific User Authorization Template by its ID. | View API |
| Update User Authorization Template | Updates an existing User Authorization Template. | View API |
| List User Authorization Templates | Searches and filters User Authorization Templates with pagination support. | View API |
| Create User Authorization Request | Creates a new authorization request using a User Authorization Template. | View API |
| List User Authorization Requests | Retrieves authorization requests for the authenticated user. | View API |
| Approve or Reject Authorization Request | Approves or rejects an authorization request. Only approvers defined in the template can approve requests. | View API |
Troubleshooting
Template Not Visible
- Check template status (must be
activefor non-admin users) - Verify user is in
allowedRequestors(actorSubs or groupFilters) - Admin users can see all templates regardless of status
Request Stuck at "Pending"
- Verify approvers exist and match template rules
- Check approvers are in correct groups with required roles
- For sequential approval, ensure previous approvers have approved
Permissions Not Assigned
- Check
validFromdate - must be current or past date - Wait for system task to process (runs periodically)
- Verify request status is
granted
Cannot Create Request
- Verify user matches
allowedRequestorsrules - Check template status is
active - If requesting for self, ensure
self: truein template
Use Cases
For detailed real-world scenarios showing how to bundle multiple groups and roles into enterprise functions, see: Use Cases
Quick Start
Prerequisites
- cidaas tenant with enabled authManager Add-On
- Admin access to create apps and manage users
- Required scopes:
cidaas:userauth_mgmt,groups,email,profile,openid
Setup
- Create Application (Web Application type)
- Configure scopes:
cidaas:userauth_mgmt,groups,email,profile,openid - Create a custom restriction group to define which users can access this portal.
- Assign admin role: Add
AUTHTEMPLATE_ADMIN_GROUPMAPto authorized users - Access dashboard:
https://{{your-domain}}/auth-manager/{{clientName}}
Help and support
Please contact us directly on our support page.